Very quick post on how to resize a VirtualBox virtual disk.

When using QCOW based disks with Virtual Box there’s no automagic method for resizing the disks. Because of that you first have to convert it. Here’s the commands you need…
Very quick post on how to resize a VirtualBox virtual disk.

When using QCOW based disks with Virtual Box there’s no automagic method for resizing the disks. Because of that you first have to convert it. Here’s the commands you need…
I thought a wee article on what a server is and why they are expensive compared to your average PC might be interesting. When you hear someone say they have built a server for the house what they usually mean to say is they’ve built a PC and have it running various applications which serves ‘stuff’. A real server is a different beast all together.

So what makes a server a server? It boils down to the hardware feature set. Sure, you can get low-end servers which are nothing more than a PC in a fancy rack mount chassis, but lets take a look at higher end goodness.
Following on from my post about ASD versions I’m going to add a couple of board schematics to this post. Anyone who has tried to fix a laptop will know getting a free copy of the schematics is half the battle. I have loads of these but this is a good start.
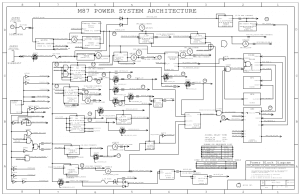
Included in PDF format are Macbook Air A1304 (MLB M96), Macbook Pro A1278 (K24, 820-2530), Macbook M42B,
As I kept finding myself hunting for the correct version of Apple Service Diagnostics I needed for which model of Mac, I’ve included a fairly recent list in this post.
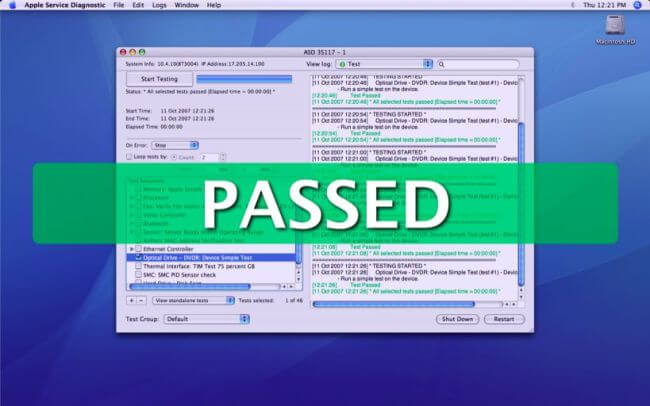
Here’s the list of Mac models and required ASD versions…
Reballing GPUs seems to be what all the cool kids are into these days. They make the claim that a dead GPU can be repaired by reballing it. What they aren’t telling you, or don’t realise themselves, is neither did it need reballed nor is it now repaired. Maybe it’s the easy money or maybe they just like the temporary smile on the customer’s face. Lets not beat about the bush though – it’s bollocks and don’t pay for it.

When a high performance chip, such as a GPU, is working hard it heats up. It heats up because it’s drawing high current and the energy dissipates as heat. When it’s off or idle it cools down. Over time this constant change in temperature causes its internal circuitry to start decaying. At high temperatures the tracks (or ‘bumps’) in a flip-chip design BGA chip physically deform and you end up with a dead chip.
Being able to direct sound is useful in many situations. Two examples are at a museum where people standing in front of two different exhibits can hear two different commentaries or at home if you don’t want to hear the crap someone else listens to.
This is where modulated ultrasound comes to the rescue – the ability to direct sound with an impressive 5 – 10° spread – that’s unheard of with any traditional loudspeaker.
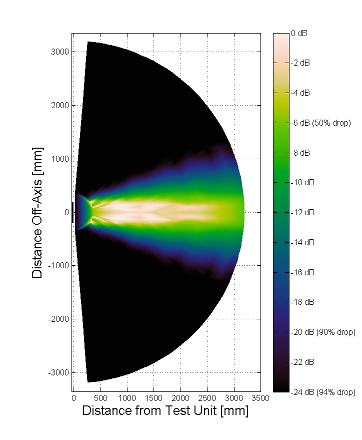
Lets take a quick look at how this craziness works because it’s not your typical transducer, that’s for sure.
This will be a quick tutorial on how to configure an Exit Node for the Tor Network. Doing this comes with some inherent risks for the operator but exit nodes are essential for bridging Tor with the ‘clear net’. Without exit nodes, anyone suffering from ISP filtering or those not wishing to have their Internet activity logged (BBC Article) couldn’t utilise Tor to access the Internet.
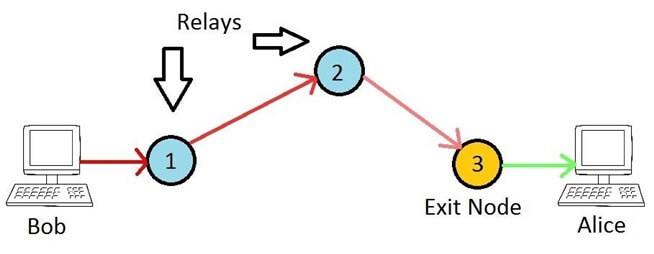
Unlike bridges, exit nodes (and normal relays) are publicly known devices, for which their IP address and configuration is available for anyone to see. They effectively make the final connection to the destination on behalf of the originating (anonymous) client. The Tor network is drastically short of exit nodes, but for good reason. Because they are the final hop in the chain, they will be making hundreds of outbound connections to whatever website or service Tor users request. It is therefore easy for the powers who be to blame an exit node operator for ‘doing bad things’ when in fact their node is merely participating in a network, much like a traditional router would in any network. Anyway, assuming you have balls of steel and willing to run an exit node I’ll take a look at how to do this with least hassle as possible.
Tor (‘The Onion Router’) is by far the most popular solution for anonymous browsing, with over 6000 relays and 2.5 million active users. I’m going to look at how to configure Tor on your network, in a variety of ways. The so called ‘Dark Web’ seems to get a bad press, maybe because of illegal sites like Silkroad, but it’s actually an invaluable resource for citizens or visitors to countries who have severe Internet censorship (including the UK!). Even Facebook has a .onion address, as does the DuckDuckGo search engine and Aphex Twin’s ‘Syro’ album.

By far the simplest and most secure way of using Tor is to install the Tor Browser. It’s dead simple and takes literally a few minutes. However, depending on your goal, there are other ways to use Tor. I’m going to look at a few ways to deploy Tor, including the pros and cons of each. These are:
As the UK government have announced they wish to classify Internet access as a public utility (implying it shouldn’t be a privilege but should be more like electricity etc) I thought I’d share how I have opened my Internet connection for anyone to use. As long as you can receive the signal you can connect and browse to your heart’s content without any keys or passwords.

Firstly, this is against the T&C’s of most ISPs, including mine. There’s a few (il)logical reasons for that but it’s mainly revenue protection. Even though they know a single connection would be perfectly suitable for many households to share, they would obviously lose money if everyone did that. Namely because, unlike other utilities, Internet access is generally not metered, meaning it’s a fixed cost per household per month. If your neighbour cannot afford their own Internet access or for whatever reason cannot get a contract then I feel it’s only fair to allow them to use mine. With talk of some people not being able to afford heating during the winter it’s hardly appropriate to expect them to also afford broadband. Who needs Internet access though? I mean it’s not like online shopping is generally cheaper or anything, not to mention almost everything is moving towards e-billing, right?
I’m not going to suggest everyone should just blindly open up their WiFi router for anyone to use but here’s how I’ve achieved this safely.
We are going to look at how to implement advert blocking on an Edgerouter at a network level using DNS. This can also be applied to other software routing devices. There are many ways to block adverts these days – various browser plugins, browsers with built in blocking, proxy servers (normal or transparent) and also with DNS. Whatever your thoughts are regarding websites using adverts for revenue generation, the fact is many sites have obscene amounts of ads.

Quite often adverts are designed to dupe you by purposely making them look like the link you are actually after. A typical example of this is where you have a ‘download’ button which is actually an advert to download something else entirely. This is not only deceitful but is down right unacceptable. Until all adverts become unobtrusive, targeted and honest I will keep blocking them; even if this means I can’t access websites which block you for blocking ads.