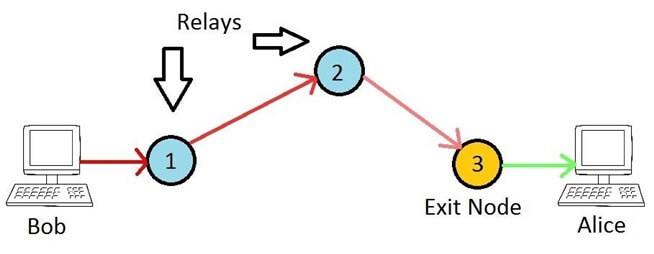
Tor (‘The Onion Router’) is by far the most popular solution for anonymous browsing, with over 6000 relays and 2.5 million active users. I’m going to look at how to configure Tor on your network, in a variety of ways. The so called ‘Dark Web’ seems to get a bad press, maybe because of illegal sites like Silkroad, but it’s actually an invaluable resource for citizens or visitors to countries who have severe Internet censorship (including the UK!). Even Facebook has a .onion address, as does the DuckDuckGo search engine and Aphex Twin’s ‘Syro’ album.

By far the simplest and most secure way of using Tor is to install the Tor Browser. It’s dead simple and takes literally a few minutes. However, depending on your goal, there are other ways to use Tor. I’m going to look at a few ways to deploy Tor, including the pros and cons of each. These are:
- Using the Tor Browser Bundle
- Configuring a Tor SOCKS proxy
- Creating a transparent Tor network
Read More »