As the UK government have announced they wish to classify Internet access as a public utility (implying it shouldn’t be a privilege but should be more like electricity etc) I thought I’d share how I have opened my Internet connection for anyone to use. As long as you can receive the signal you can connect and browse to your heart’s content without any keys or passwords.

Firstly, this is against the T&C’s of most ISPs, including mine. There’s a few (il)logical reasons for that but it’s mainly revenue protection. Even though they know a single connection would be perfectly suitable for many households to share, they would obviously lose money if everyone did that. Namely because, unlike other utilities, Internet access is generally not metered, meaning it’s a fixed cost per household per month. If your neighbour cannot afford their own Internet access or for whatever reason cannot get a contract then I feel it’s only fair to allow them to use mine. With talk of some people not being able to afford heating during the winter it’s hardly appropriate to expect them to also afford broadband. Who needs Internet access though? I mean it’s not like online shopping is generally cheaper or anything, not to mention almost everything is moving towards e-billing, right?
I’m not going to suggest everyone should just blindly open up their WiFi router for anyone to use but here’s how I’ve achieved this safely.
First and foremost the only safe way to do this is to separate out the free WiFi from your own private network. You could do this with multiple physical Access Points but I’ve done it with a single enterprise-grade Access Point. Some consumer grade hardware also allow multiple SSIDs and providing they also allow network segregation you could achieve the same.
The hardware:
- Virgin Media ‘super hub’ running in Modem mode
- EdgeRouter Lite
- ZyXEL NWA1100-NH
- TP-Link VLAN capable gigabit Switch
As well as segregating my home network and I’ve also done something a bit unusual here – routed all WiFi traffic out of a VPN connection. This is so anyone connected to it has no idea they are using my home broadband connection.
First up we need two VLANs, one for the private LAN and one for the Free WiFi. On the Edgerouter configure a vif for the WiFi. I’ll assume you already have your LAN working so this is the additional vif:
interfaces {
ethernet eth1 {
vif 10 {
address 192.168.255.1/24
description "Guest WiFi"
firewall {
in {
modify source-wls
}
local {
name basic1
}
out {
name guest
}
traffic-policy {
in guest-up
out guest-down
}
}
You can see here the ‘in’ firewall is actually a modify set – this is because we are going to do something a bit sneaky.
rule 10 {
action modify
description "Send traffic from Free WiFi over VPN"
modify {
table 1
}
source {
address 192.168.255.0/24
}
}
This will send all traffic from 192.168.255.0/24 (Free WiFi clients) to our ‘table 1’ routing table.
interface-route 0.0.0.0/0 {
next-hop-interface vtun0 {
}
}
Table 1 sets the next hop interface to be ‘vtun0’ which is a VPN connection.
config-file /config/auth/wls/wls.ovpn
description "WLS VPN"
firewall {
local {
name basic1
}
}
The file ‘wls.ovpn’ contains our configuration for this VPN connection. You can do this config directly in EdgeOS if you wish but essentially it’s just an OpenVPN connection which you can get from numerous providers. In my case it’s a Virtual Machine I have elsewhere doing other various tasks.
The reason for directing traffic over the VPN like this is so anyone connected on the Free WiFi connection does not use my IP address as the source – they have the public IP of the VPN connection. A little sneaky I admit but it’s not detrimental to anyone and means anyone connected to the WiFi knows nothing about my Internet connection (who the ISP is, what my IP is etc).
We also have some bandwidth limiting (traffic policy). These look like this.
limiter guest-up {
default {
bandwidth 256kbit
burst 15k
}
description "Guest WiFi Upload Limiter"
}
shaper guest-down {
bandwidth 20mbit
default {
bandwidth 50%
burst 15k
ceiling 100%
queue-type fair-queue
}
description "Guest WiFi Download Shaper"
}
Here we are limiting the upload to 256kbit and download to 20mbit. Given I have 100mbps download bandwidth, 20mbit is 1/5th – that is both generous and does not affect me in the slightest. Keeping the upload limit to 256kbps is essential given it’s an asymmetric connection.
Lastly we have a firewall specified for the ‘out’ direction – this is so any machines on other networks, including my private LAN, cannot connect to any of the WiFi clients. There are similar firewalls on the other LANs to prevent WiFi clients connecting to them either.
default-action drop
description "Default est/rel for guest wifi"
rule 1 {
action accept
state {
established enable
invalid disable
new disable
related enable
}
}
What we now have is VLAN 10 connected on the Edgerouter which is tagging packets on eth1. Next we need to configure the switch and tag VLAN 10 on both the Edgerouter port and the Access Point port.
In this case port 8 is the Edgerouter and port 9 is the Zyxel Access Point.
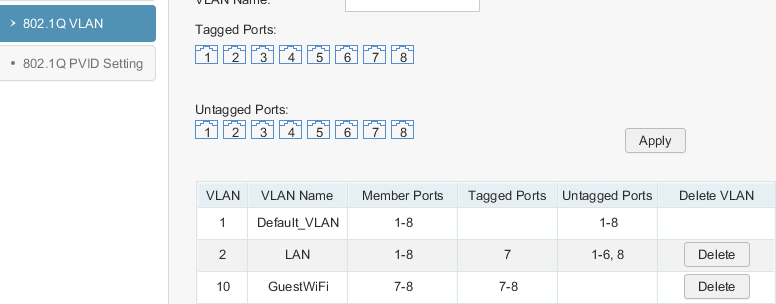
Finally we need to configure a second SSID on the AP and ensure it is tagging VLAN 10. Note that intra-BSS blocking is enabled to prevent WiFi clients from talking to each other. This is important as anyone connecting should expect a basic level of security in place. Preventing clients from communicating is a good way to provide isolation from each other. As we only have one Access Point this effectively means clients can only communicate with the router, thus the Internet. If you were to have multiple Access Points you need to think about this a bit more. Some switches allow ‘edge’ ports to only talk to the ‘uplink’ ports which is a very similar concept.

There is no Security profile as this SSID is open and unencrypted.

BSSID2 has VLAN 10 assigned
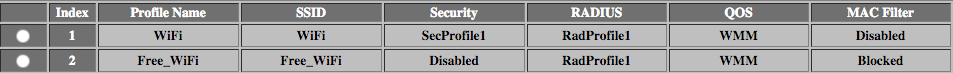
That’s all there is to it.
You can test this all works by connecting to the Free WiFi SSID and ensure that your IP address is that of the VPN connection. It is also worth checking that two clients cannot communicate with each other and that the traffic shaping is working (speedtest.net should suffice).
A test to ensure guest clients can’t talk to anything else, including your private LAN is also a must – this should also include the router and AP’s management interfaces.
Proving Free WiFi isn’t difficult and I hope I’ve demonstrated it can be achieved safely and securely. I encourage anyone confident enough with this to go ahead and do it 🙂