For a casual bit of weekend fun I thought I’d share a potential method for obtaining your neighbour’s Facebook password. This is purely educational and I used my own systems to do this but it highlights how potentially easy it can be to obtain someone’s login credentials to any website.

We are going to utilise various attack vectors to demonstrate the methodology of the process. The story starts with a hypothetical situation.
You live in a semi-detached house somewhere in suburban Scotland. You have a partner who you have been going out with for 47 years. A new next door neighbour moves in who seems to be taking a fancy to your partner. After a few months you suspect they’re getting down and dirty whilst you’re at work. Intrigued to find out more you decide you want to see your neighbour’s Facebook private messages. Ho hum, this could get messy but you don’t care – you’re pissed and going for gold.
First off you notice the neighbour’s WiFi network is within range. You know it’s theirs as there’s only yours and theirs showing up in available networks – that’s lucky.
We need a way to start sniffing their wireless traffic.
Lets break out KisMAC – this handy piece of software can be used to crack WEP and WPA encryption on a Mac. It’s intended to verify how secure your own equipment is and should never be used for anything illegal. There are many alternatives for Linux and Windows. Your neighbour is a bit old school and opted for WEP encryption. This is ideal as it means we don’t need to brute force with a dictionary attack – instead KisMAC can use Weak Scheduling Attack to find the keys.
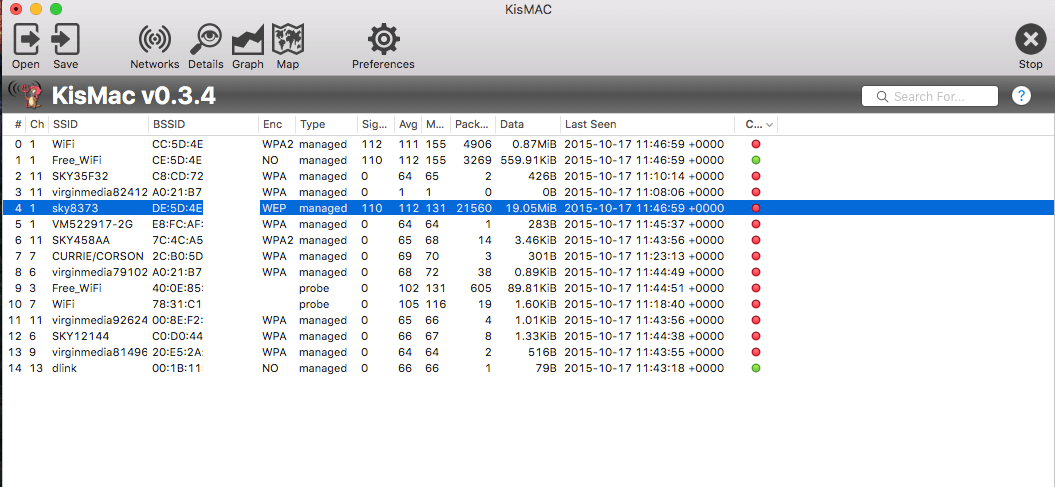
Lets fire it up and see what SSIDs we have – we are looking for ‘sky8373’ as that’s the neighbour.
You will notice your machine has lost connection to any wireless networks as it’s now in monitor mode.
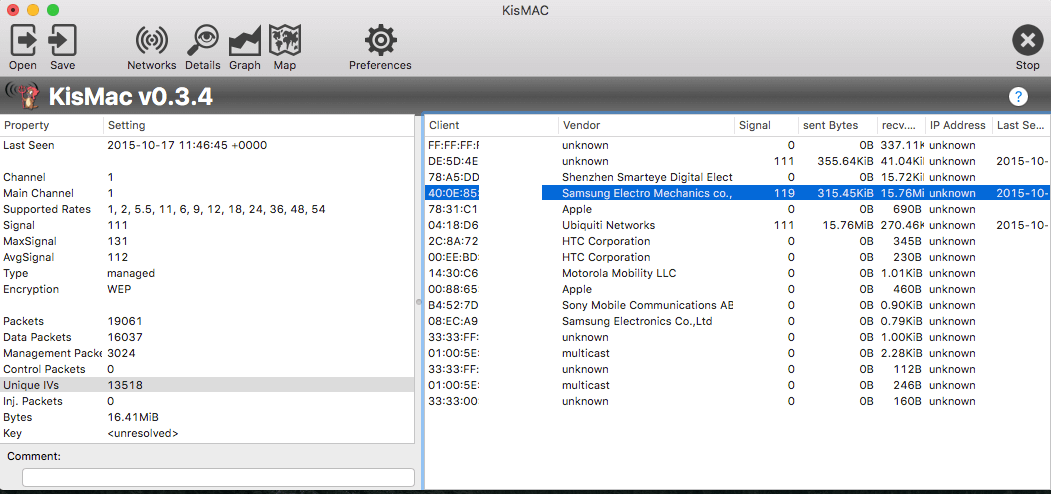
Cool! We can see it in the list and also see it’s using WEP encryption. If we double click it we can see a bit more information along with a list of clients.
It’s important to note which channel it is using. What we’re going to be doing is collecting as many unique IVs (initialisation vectors) as we can. These are fixed size inputs to a cryptographic primitive and are essentially random strings which we collect in order to proceed.
The rate at which we can collect IV’s is determined by the throughput of data on the network. If the neighbour only looks up Google News once a day we may need to wait days, if not weeks to have enough IV’s to worth with. This method is known as passive sniffing but there is an alternative called injection, which is many times faster but requires compatible wireless hardware. They’re not expensive (£40 for a HWUG1) but lets assume your neighbour likes to watch Netflix. In this case the ~200MB you need to capture will happen in a matter of minutes.
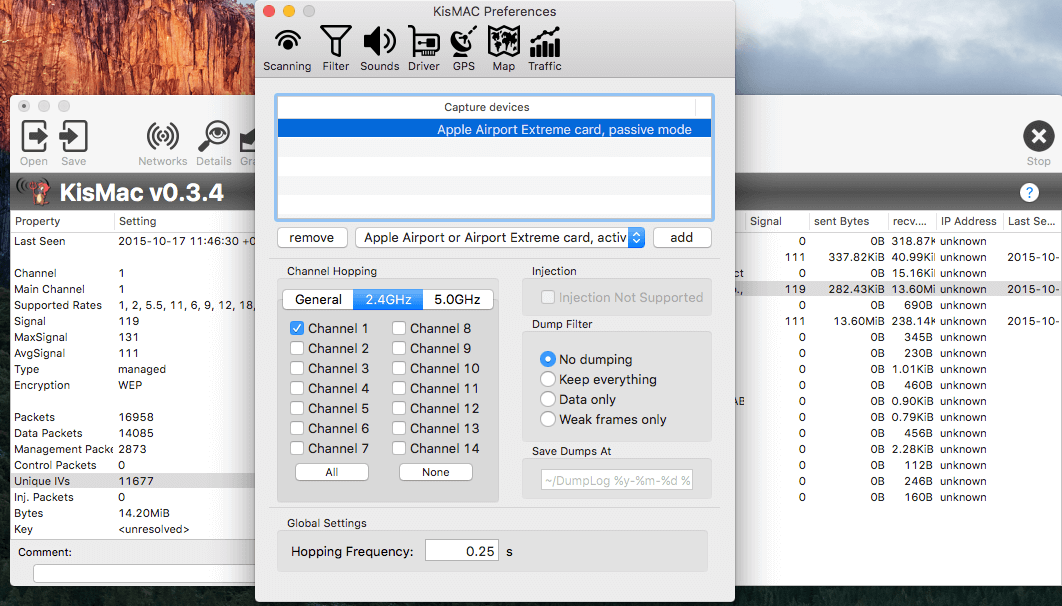
Ensure that you are only sniffing on the channel which the AP is operating on, so uncheck all other channels. If you don’t do this it will take an eternity to collect IVs as it cycles through all available channels.
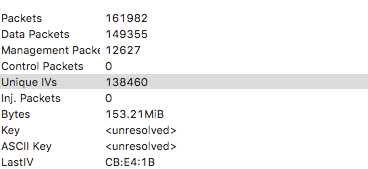
We are looking for at least 130,000 IV’s – the more the better.
Here we can see we have reached around 140,000 with 150MiB of sniffed data.
Woohoo we’re good to go. Next, within KisMAC go to:
Network -> Crack -> Weak Scheduling Attack -> Against Both
With any luck, after a few minutes, you will see a message to say complete.
If we were brute forcing a WPA network we would see this while it’s trying the dictionary:
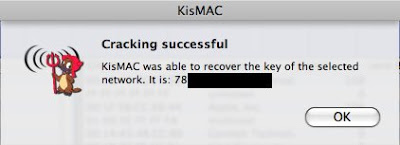
Great so now we have our neighbour’s preshared key. This means we can use it to sniff all WiFi traffic on their network. We’re going to do this because we need a way to read the username and password they use to log in to websites.
Our next tool is Wireshark – this program will capture and analyse network traffic. Once installed, fire it up.
We want to listen for traffic on the en1 interface on a Mac as this is usually the WiFi adapter. Because we don’t just want to monitor traffic on the local interface (we want to see everything on their WiFi network!) you need to set the adapter to monitor ‘enabled’ in preferences.
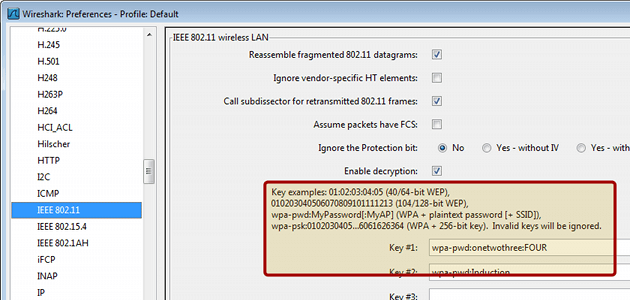
We know this network is WEP encrypted so we will need to Wireshark our previously cracked key. Go to Edit->Preferences->IEEE 802.11 and you should see these options:
Enter the key and you are good to go.
Set the capture to start running – you will see any traffic flowing on the WiFi network. The important point to remember is although the traffic is decrypted at the physical layer (i.e. the same as if it were an ‘open’ wireless network) there is still likely to be encryption of data flowing to websites by means of SSL.
There is no point in attempting to crack SSL unless the website is using known weak ciphers. All major websites should now strictly be using TLS. It’s possible poorly maintained web servers will still be using SSLv2/SSLv3. Lets assume the neighbour only seems to visit strongly encrypted websites.
As we know there is no point is trying to crack Facebook’s SSL traffic so instead we’re going to find a way to get their login details. The logic here is quite simple – most people use the same password for multiple sites.
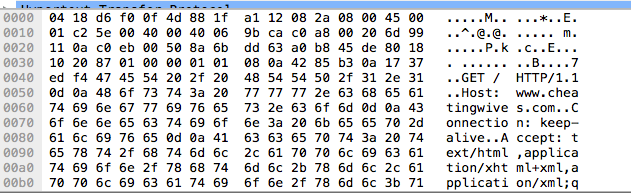
First off lets have a good sniff about their traffic and see what we find. Let’s look for non-SSL traffic by setting a filter in wireshark.. enter this in the filter bar:
tcp.port == 80
This looks interesting, what do we have here?!
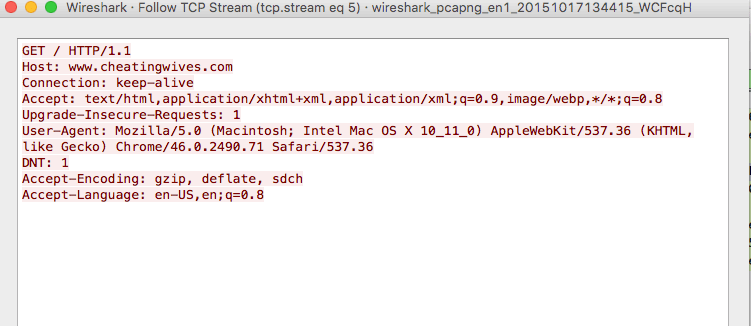
This is a GET request to an HTTP website with a curious name – www.cheatingwives.com. This is worth a look.
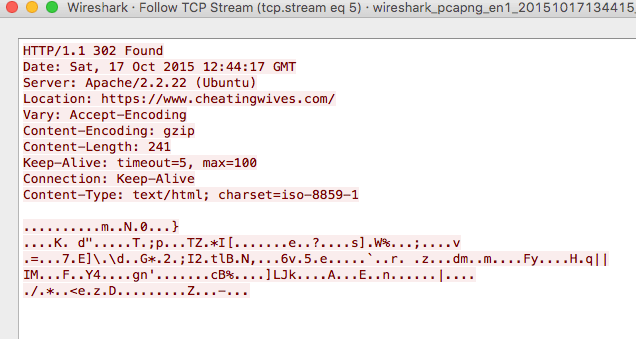
Following the stream we see:
The response back from the GET request was HTTP code 302 which means redirect – in this case to the HTTPS site. That’s ok we can still have a look at the site for ourselves.
Note: This intermediary website could be any insecure site. It would be even easier if the site’s login mechanism was unencrypted in the first place (HTTP).
At this stage, if we wanted, we could also use his Internet connection to perform the next steps. This would mean that all traffic going to the site will originate from his IP, not ours. Go ahead and connect to your neighbours WiFi using the key from earlier.
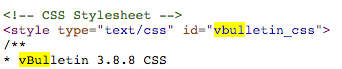
The website appears to be some kind of forum for cheating house wives. This could be interesting. Lets have a look at the source code and see what forum software it’s using.
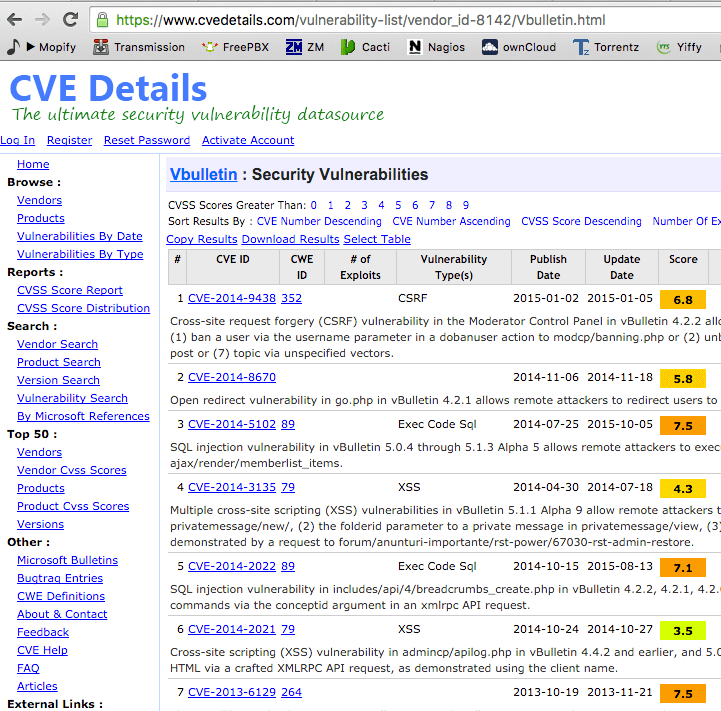
We now know the website runs vBulletin version 3.8.8 and we also know there is a good chance the neighbour has an account with them.
Lets check if there’s any known exploits for it.
Oh would you believe it there’s a shit tonne of them.
What we could try is using a ‘local file include’ exploit and see if we can locate their SSL private key. Of course if we have a local file exploit we could probably grab the vBullitin config and get direct DB access etc but let’s keep this a network based exploit.
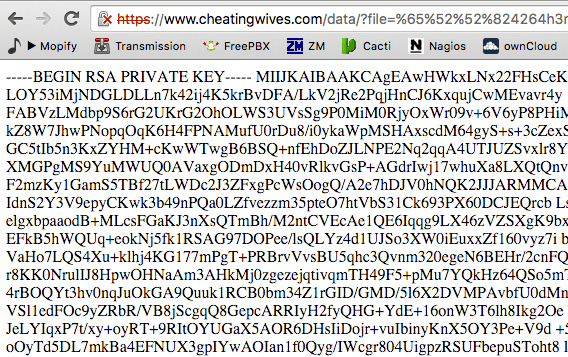
It seems we can indeed use a known exploit and get their SSL key.
Now we really are feeling naughty. Having this key means we can now decrypt all of our neighbour’s traffic with this website. Let’s go ahead and do that.
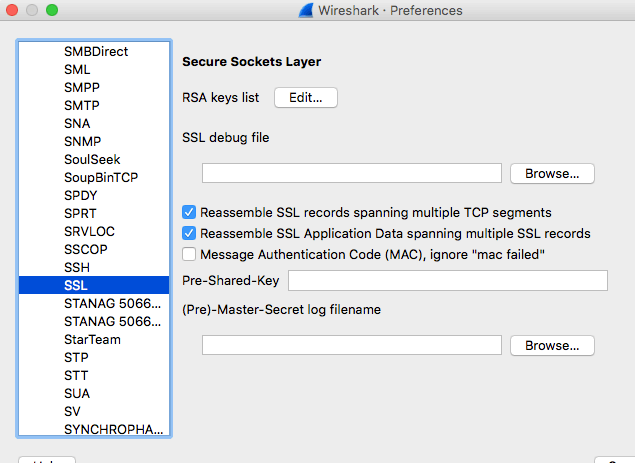
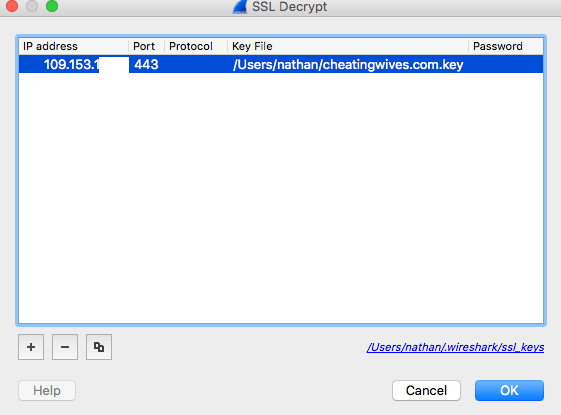
Back to wireshark again. We need to add this key so wireshark uses it for all SSL traffic to cheatingwives.com. Under preferences -> protocols -> SSL
Click Edit and add the key for the IP address of the site (use dig or host or whatever to get the IP).
This now means whenever the neighbour visits the website and we have wireshark running we can see, in plain text, all data sent between his computer and the server.
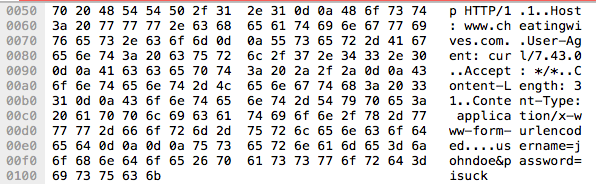
After dinner something interesting has appeared.
Well fuck me – that’s perfect. What we have here is an HTTP POST request to the website with his username and password (johndoe / isuck).
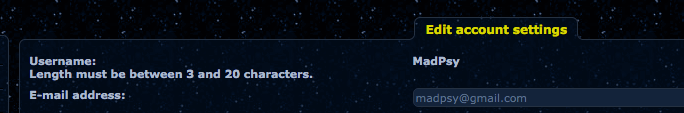
This means we can reconnect to his WiFi and log in as him. Let’s have a look at his profile settings.
Funnily enough he has the same nickname as me.. ha what’s the chances of that.
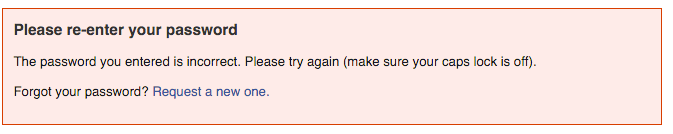
Ok so now we know his e-mail address too. Facebook logins are e-mail based so lets give that a go.
Dammit, that didn’t work. Aha but maybe his e-mail password is the same. Let’s try that!
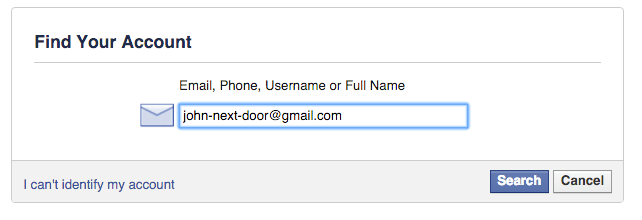
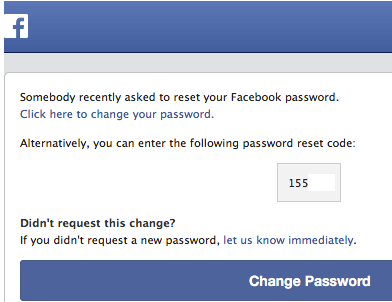
Woohooo we’re in!! Now lets try a password reset on the neighbour’s Facebook account.
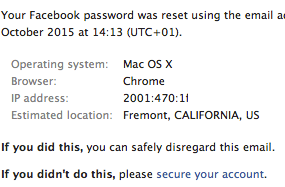
Great success! We have reset his facebook password and can now log into his account to read all private messages.
Lucky for the neighbour your partner was not in their list of contacts but had that been any different there would be trouble I’m sure!
Now for the important lessons learned from this.
- Use WPA2 encryption for your wireless router (wouldn’t have stopped this but would have slowed it down)
- If you run a website, especially when it runs forum software, ensure it is up to date.
- If you run an SSL site ensure it only uses TLS 1.2 and make sure only ‘root‘ can read the SSL private key
- Ensure you use Facebook’s two-factor-authentication.
- Ensure you use your e-mail provider’s two-factor-authentication (Gmail, Hotmail, Yahoo)
- Try not to use the same password on multiple sites – at the very least your e-mail password should be unique
- If a website’s login page is over HTTP either don’t use the site or ensure the password you use is only for that website.
- Never actually try to attempt this – it’s illegal
Well that was fun wasn’t it 🙂 Remember to be good boys and girls!
In case it wasn’t obvious I didn’t actually ‘hack’ anything here as for one it was all my own stuff and two it was only a demonstration of the theory (cheatingwives.com was entirely fictional).